Cracking Mifare Classic
29 Jan 2017, 13:27 This post summarizes my experience with cloning RFID cards that I am using on daily basis. There is nothing new here, just a summary of well-known hacks that I found on the internet. Corporate badge At work we use 125KHz passive RFID badges which are easy to clone. Each badge has unique ID, so the first step is to read this ID. Harry Houdini Kon Kan Mp3 Download. I have been using this DIY based on an Arduino: By the way, I had to make some slight to the firware to make it work. Once you get the ID, you can “program” it on an ATtiny85 microcontroller as described.
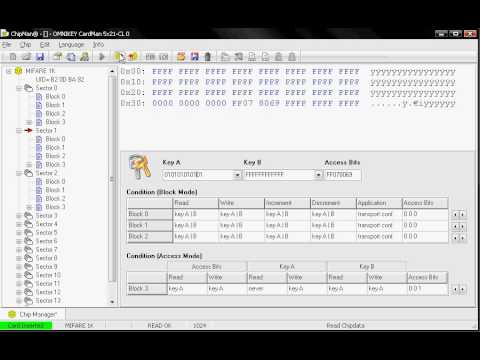
Dhoondte Reh Jaoge Yaar Hamare Jaisa Mp3 Song Download. This is how my assembled clone looks like: Residential entry The building where I live (and many other buildings) has a front door which is opened with an NFC tag. I found that it is Mifare Classic 1k tag which has been cracked long time ago. Rslogix 5000 V21 Activation Crack. Actually, it turned out that I don’t have to crack anything to create a clone because the tag had default keys.
In this blog post I will cover some quick basics about NFC, Mifare Classic and how to set up everything for reading and writing a NFC tag. At the end I show you how to reprogram a vending machine's NFC tag to contain more credits. NFC stands for Near Field Communication and is used to communicate. A Professional and easy to use Mifare Application. RFID Cooking with Mifare Classic. DISCLAIMER: The information and reference implementation is provided.
They were relying only on the fact that each tag has unique ID and the door opens when pre-recorded ID is shown. Some fine people in China are selling tags that you can program with whatever ID you want, so creating is a clone a simple matter of running nfc-mfsetuid: Public transport Turns out that Mifare Classic 1k is also being used for the public transport in Sofia. I managed to crack one of the old cards that I have – it has been using a combination of default keys and “SofiaM”: However, some of the new cards for the subway manage to resist my cracking attempts. I guess they are using something more secure which is running an emulation of Mifare Classic.
UPDATE: No, they are not. Keys have been disclosed.