Rootkit Ntoskrnl Execution
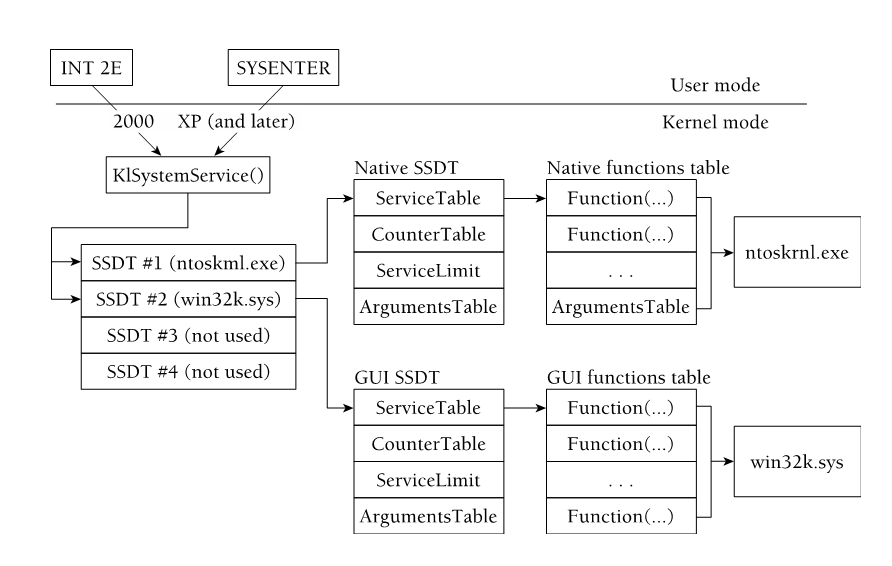
Rootkit Ntoskrnl Execution. Control the health of Windows 1. 0)Applies to. This article details an end- to- end solution that helps you protect high- value assets by enforcing, controlling, and reporting the health of Windows 1. In Bring Your Own Device (BYOD) scenarios, employees. I have scanned with Malware Bytes since the detection and found nothing but AVG keeps finding these rootkits. All i can do is give you the report im getting from AVG so here goes. C: Windows System32 Drivers spnh.sys pci.sys, hooked import ntoskrnl.exe IoAttachDeviceToDeviceStack ->spnh.sys.
Author: Greg Hoglund -------[ Phrack Magazine --- Vol. 9 Issue 55 --- 09.09.99 --- 05 of 19 ] -------------------------[ A *REAL* NT Rootkit, patching the NT Kernel ] --------[ Greg Hoglund ] Introduction ------------ First of all, programs such as Back Orifice and Netbus are NOT rootkits.
They are amateur versions of PC-Anywhere, SMS, or a slew of other commercial applications that do the same thing. If you want to remote control a workstation, you could just as easily purchase the incredibly powerful SMS system from Microsoft. A remote-desktop/administration application is NOT a rootkit.
What is a rootkit? A rootkit is a set of programs which *PATCH* and *TROJAN* existing execution paths within the system. This process violates the *INTEGRITY* of the TRUSTED COMPUTING BASE (TCB). In other words, a rootkit is something which inserts backdoors into existing programs, and patches or breaks the existing security system. - A rootkit may disable auditing when a certain user is logged on.
- A rootkit could allow anyone to log in if a certain 'backdoor' password is used. - A rootkit could patch the kernel itself, allowing anyone to run privileged code if they use a special filename. The possibilities are endless, but the point is that the 'rootkit' involves itself in pre-existing architecture, so that it goes un-noticed. A remote administration application such as PC Anywhere is exactly that, an application.
A rootkit, on the other hand, patches the already existing paths within the target operating system. To illustrate this, I have included in this document a 4-byte patch to the NT kernel that removes ALL security restrictions from objects within the NT domain. If this patch were applied to a running PDC, the entire domain's integrity would be violated. If this patch goes unnoticed for weeks or even months, it would be next to impossible to determine the damage. Network based security & the Windows NT Trust Domain ---------------------------------------------------- If you know much about the NT Kernel, you know that one of the executive components is called the Security Reference Monitor (SRM). The DoD Red Book also defines a 'Security Reference Monitor'.
We are talking the same language. In the Red Book, a security domain is managed by a single entity. To Quote: 'A single trusted system is accredited as a single entity by a single accrediting authority. A ``single trusted system' network implements a reference monitor to enforce the access of subjects to objects in accordance with an explicit and well defined network security policy [DoD Red Book].' In NT parlance, that is called the Primary Domain Controller (PDC). Remember that every system has local security and domain security.
In this case, we are talking about the domain security. The PDC's 'Security Reference Monitor' is responsible for managing all of the objects within the domain.
Hbgary Responder Community Edition. In doing this, it creates a single point of control, and therefore a 'single trusted system' network. How to violate system integrity ------------------------------- I know this is alot of book theory, but bear with me just a bit longer. The DoD Orange Book also defines a 'Trusted Computing Base' (TCB). If you are an NT programmer, then you have likely worked with the security privilege SE_TCB_PRIVILEGE. Xjz Survey Remover Permission Key Download. That privilege maps to the more familiar 'act as part of the Operating System' User-Right.
Using the User Administrator for NT you can actually add this privilege to a user. If you have the ability to act as part of the TCB, you can basically do anything. There is very little security implemented between your process and the rest of the machine. If the TCB can no longer be trusted, then the integrity of the entire network system is shot. The patch I am about to show you is an example of this. The patch, if installed on a Workstation, violates a network 'partition'.